★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW GCIA Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/GCIA-dumps.html
Want to know Certleader GCIA Exam practice test features? Want to lear more about GIAC GIAC Certified Intrusion Analyst certification experience? Study Highest Quality GIAC GCIA answers to Refresh GCIA questions at Certleader. Gat a success with an absolute guarantee to pass GIAC GCIA (GIAC Certified Intrusion Analyst) test on your first attempt.
Check GCIA free dumps before getting the full version:
NEW QUESTION 1
You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server2008 network environment. The network is configured as a Windows Active Directory-based single forest single domain network. The network is configured on IP version 6 protocol. All the computers on the network are connected to a switch device. One day, users complain that they are unable to connect to a file server. You try to ping the client computers from the server, but the pinging fails. You try to ping the server's own loopback address, but it fails to ping. You restart the server, but the problem persists.
What is the most likely cause?
- A. The switch device is not workin
- B. The cable that connects the server to the switch is broke
- C. Automatic IP addressing is not workin
- D. The server's NIC is not workin
- E. The server is configured with unspecified IP addres
Answer: D
NEW QUESTION 2
You work as a professional Computer Hacking Forensic Investigator for DataEnet Inc. You want to investigate e-mail information of an employee of the company. The suspected employee is using an online e-mail system such as Hotmail or Yahoo. Which of the following folders on the local computer will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
- A. History folder
- B. Download folder
- C. Cookies folder
- D. Temporary Internet Folder
Answer: ACD
NEW QUESTION 3
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
Each correct answer represents a complete solution. Choose all that apply.
- A. Dig
- B. Host
- C. NSLookup
- D. DSniff
Answer: ABC
NEW QUESTION 4
The promiscuous mode is a configuration of a network card that makes the card pass all traffic it receives to the central processing unit rather than just packets addressed to it. Which of the following tools works by placing the host system network card into the promiscuous mode?
- A. NetStumbler
- B. Snort
- C. THC-Scan
- D. Sniffer
Answer: D
NEW QUESTION 5
Which of the following ports is used by NTP for communication?
- A. 143
- B. 123
- C. 161
- D. 53
Answer: B
NEW QUESTION 6
Which of the following is the default port used by Simple Mail Transfer Protocol (SMTP)?
- A. 80
- B. 25
- C. 20
- D. 21
Answer: B
NEW QUESTION 7
Ryan, a malicious hacker submits Cross-Site Scripting (XSS) exploit code to the Website of Internet forum for online discussion. When a user visits the infected Web page, code gets automatically executed and Ryan can easily perform acts like account hijacking, history theft etc. Which of the following types of Cross-Site Scripting attack Ryan intends to do?
- A. SAX
- B. Persistent
- C. Document Object Model (DOM)
- D. Non persistent
Answer: B
NEW QUESTION 8
Who are the primary victims of smurf attacks on the contemporary Internet system?
- A. FTP servers are the primary victim to smurf attacks
- B. IRC servers are the primary victim to smurf attacks
- C. SMTP servers are the primary victim to smurf attacks
- D. Mail servers are the primary victim to smurf attacks
Answer: B
NEW QUESTION 9
Peter works as a Computer Hacking Forensic Investigator. He has been called by an organization to conduct a seminar to give necessary information related to sexual harassment within the work place. Peter started with the definition and types of sexual harassment. He then wants to convey that it is important that records of the sexual harassment incidents should be maintained, which helps in further legal prosecution. Which of the following data should be recorded in this documentation?
Each correct answer represents a complete solution. Choose all that apply.
- A. Names of the victims
- B. Date and time of incident
- C. Nature of harassment
- D. Location of each incident
Answer: ABD
NEW QUESTION 10
Which of the following tools is a wireless sniffer and analyzer that works on the Windows operating system?
- A. Aeropeek
- B. Void11
- C. Airsnort
- D. Kismet
Answer: A
NEW QUESTION 11
HOTSPOT
You work as a Network Administrator for McRobert Inc. The company's Windows 2000-based network is configured with Internet Security and Acceleration (ISA) Server 2000. You are configuring intrusion detection on the server. You want to get notified when a TCP SYN packet is sent with a spoofed source IP address and port number that match the destination IP address and port number. Mark the alert that you will enable on the Intrusion Detection tab page of the IP Packet Filters Properties dialog box to accomplish the task. 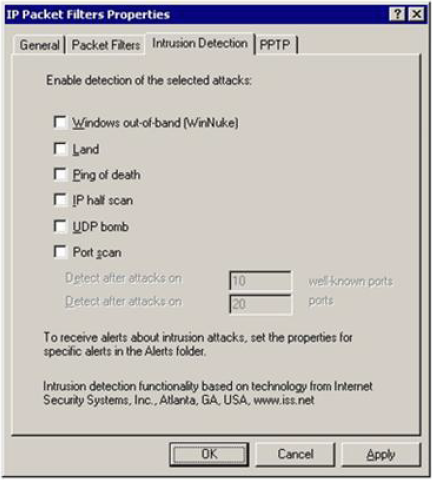
Solution:
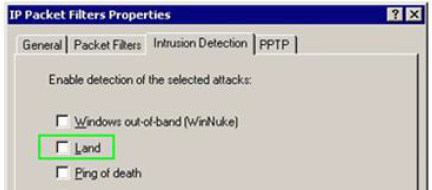
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 12
Which of the following Web attacks is performed by manipulating codes of programming languages such as SQL, Perl, Java present in the Web pages?
- A. Command injection attack
- B. Code injection attack
- C. Cross-Site Request Forgery
- D. Cross-Site Scripting attack
Answer: B
NEW QUESTION 13
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. John wants to redirect all TCP port 80 traffic to UDP port 40, so that he can bypass the firewall of the We-are-secure server. Which of the following tools will John use to accomplish his task?
- A. PsExec
- B. PsList
- C. Fpipe
- D. Cain
Answer: C
NEW QUESTION 14
Choose the proper transport protocol and port number used for Domain Name System. You should be concerned only with DNS lookups.
- A. tcp, port 53
- B. udp, port 53
- C. tcp, port 67
- D. udp, port 67
Answer: B
NEW QUESTION 15
Andrew, a bachelor student of Faulkner University, creates a gmail account. He uses 'Faulkner' as the password for the gmail account. After a few days, he starts receiving a lot of e-mails stating that his gmail account has been hacked. He also finds that some of his important mails have been deleted by someone. Which of the following methods has the attacker used to crack Andrew's password?
Each correct answer represents a complete solution. Choose all that apply.
- A. Buffer-overflow attack
- B. Brute force attack
- C. Dictionary-based attack
- D. Password guessing
- E. Social engineering
- F. Zero-day attack
- G. Denial-of-service (DoS) attack
- H. Rainbow attack
Answer: BCDEH
NEW QUESTION 16
Which of the following tools is used to analyze a system and report any unsigned drivers found?
- A. regedit.exe
- B. sigverify.exe
- C. sigverif.exe
- D. msconfig
Answer: C
NEW QUESTION 17
You work as a Network Administrator for Tech Perfect Inc. The office network is configured as an IPv6 network. You have to configure a computer with the IPv6 address, which is equivalent to an IPv4 publicly routable address. Which of the following types of addresses will you choose?
- A. Site-local
- B. Global unicast
- C. Local-link
- D. Loopback
Answer: B
NEW QUESTION 18
Trinity wants to send an email to her friend. She uses the MD5 generator to calculate cryptographic hash of her email to ensure the security and integrity of the email. MD5 generator, which Trinity is using operates in two steps:
Creates check file
Verifies the check file
Which of the following MD5 generators is Trinity using?
- A. Secure Hash Signature Generator
- B. Mat-MD5
- C. Chaos MD5
- D. MD5 Checksum Verifier
Answer: D
NEW QUESTION 19
You work as a Network Administrator for McRobert Inc. You plan to configure your Windows Vista computer for Internet access. To achieve this, which of the following communication protocols needs to be bound to the dial-up adapter?
- A. TCP/IP
- B. DLC
- C. NetBEUI
- D. AppleTalk
Answer: A
NEW QUESTION 20
Which of the following tools is used to detect wireless LANs using the 802.11b, 802.11a, and 802.11g WLAN standards on the Windows platform?
- A. Cain
- B. AiroPeek
- C. NetStumbler
- D. Snort
Answer: C
NEW QUESTION 21
......
P.S. Easily pass GCIA Exam with 508 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy GCIA Dumps: https://www.2passeasy.com/dumps/GCIA/ (508 New Questions)