★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW NSE6_FAC-6.4 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/NSE6_FAC-6.4-dumps.html
Our pass rate is high to 98.9% and the similarity percentage between our NSE6_FAC-6.4 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the Fortinet NSE6_FAC-6.4 exam in just one try? I am currently studying for the Fortinet NSE6_FAC-6.4 exam. Latest Fortinet NSE6_FAC-6.4 Test exam practice questions and answers, Try Fortinet NSE6_FAC-6.4 Brain Dumps First.
Check NSE6_FAC-6.4 free dumps before getting the full version:
NEW QUESTION 1
Which two features of FortiAuthenticator are used for EAP deployment? (Choose two)
- A. Certificate authority
- B. LDAP server
- C. MAC authentication bypass
- D. RADIUS server
Answer: AD
Explanation:
Two features of FortiAuthenticator that are used for EAP deployment are certificate authority and RADIUS server. Certificate authority allows FortiAuthenticator to issue and manage digital certificates for EAP methods that require certificate-based authentication, such as EAP-TLS or PEAP-EAP-TLS. RADIUS server allows FortiAuthenticator to act as an authentication server for EAP methods that use RADIUS as a transport protocol, such as EAP-GTC or PEAP-MSCHAPV2.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/wireless-802-1x-authen
NEW QUESTION 2
Which statement about the guest portal policies is true?
- A. Guest portal policies apply only to authentication requests coming from unknown RADIUS clients
- B. Guest portal policies can be used only for BYODs
- C. Conditions in the policy apply only to guest wireless users
- D. All conditions in the policy must match before a user is presented with the guest portal
Answer: D
Explanation:
Guest portal policies are rules that determine when and how to present the guest portal to users who want to access the network. Each policy has a set of conditions that can be based on various factors, such as the source IP address, MAC address, RADIUS client, user agent, or SSID. All conditions in the policy must match before a user is presented with the guest portal. Guest portal policies can apply to any authentication request coming from any RADIUS client, not just unknown ones. They can also be used for any type of device, not just BYODs. They can also apply to wired or VPN users, not just wireless users. References:
https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372404/guest-management/37240
NEW QUESTION 3
At a minimum, which two configurations are required to enable guest portal services on FortiAuthenticator? (Choose two)
- A. Configuring a portal policy
- B. Configuring at least on post-login service
- C. Configuring a RADIUS client
- D. Configuring an external authentication portal
Answer: AB
Explanation:
enable guest portal services on FortiAuthenticator, you need to configure a portal policy that defines the conditions for presenting the guest portal to users and the authentication methods to use. You also need to configure at least one post-login service that defines what actions to take after a user logs in successfully, such as sending an email confirmation, assigning a VLAN, or creating a user account. Configuring a RADIUS client or an external authentication portal are optional steps that depend on your network setup and requirements. References:
https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372404/guest-management
NEW QUESTION 4
A system administrator wants to integrate FortiAuthenticator with an existing identity management system with the goal of authenticating and deauthenticating users into FSSO.
What feature does FortiAuthenticator offer for this type of integration?
- A. The ability to import and export users from CSV files
- B. RADIUS learning mode for migrating users
- C. REST API
- D. SNMP monitoring and traps
Answer: C
Explanation:
REST API is a feature that allows FortiAuthenticator to integrate with an existing identity management system with the goal of authenticating and deauthenticating users into FSSO. REST API stands for Representational State Transfer Application Programming Interface, which is a method of exchanging data between different systems using HTTP requests and responses. FortiAuthenticator provides a REST API that can be used by external systems to perform various actions, such as creating, updating, deleting, or querying users and groups, or sending FSSO logon or logoff events.
References: https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/rest-api
NEW QUESTION 5
A device or user identity cannot be established transparently, such as with non-domain BYOD devices, and allow users to create their own credentialis.
In this case, which user idendity discovery method can Fortiauthenticator use?
- A. Syslog messaging or SAML IDP
- B. Kerberos-base authentication
- C. Radius accounting
- D. Portal authentication
Answer: D
Explanation:
Portal authentication is a user identity discovery method that can be used when a device or user identity cannot be established transparently, such as with non-domain BYOD devices, and allow users to create their own credentials. Portal authentication requires users to enter their credentials on a web page before accessing network resources. The other methods are used for transparent identification of domain devices or users. References:
https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372406/user-identity-discovery
Examine the screenshot shown in the exhibit.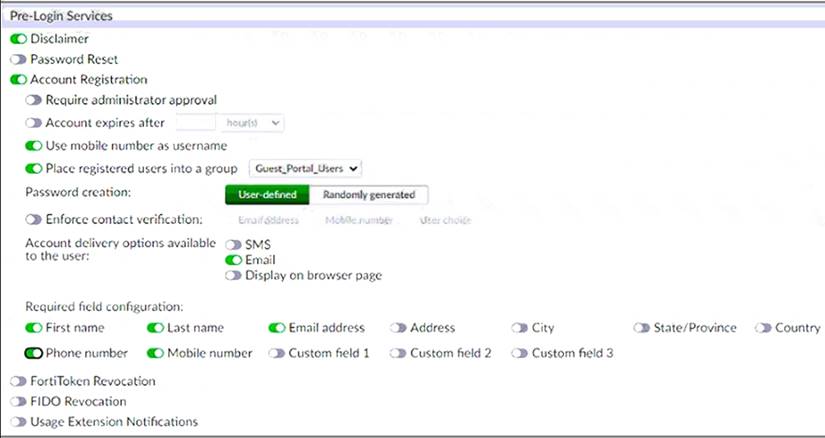
NEW QUESTION 6
You have implemented two-factor authentication to enhance security to sensitive enterprise systems. How could you bypass the need for two-factor authentication for users accessing form specific secured
networks?
- A. Create an admin realm in the authentication policy
- B. Specify the appropriate RADIUS clients in the authentication policy
- C. Enable Adaptive Authentication in the portal policy
- D. Enable the Resolve user geolocation from their IP address option in the authentication policy.
Answer: C
Explanation:
Adaptive Authentication is a feature that allows administrators to bypass the need for two-factor authentication for users accessing from specific secured networks. Adaptive Authentication uses geolocation information from IP addresses to determine whether a user is accessing from a trusted network or not. If the user is accessing from a trusted network, FortiAuthenticator can skip the second factor of authentication and grant access based on the first factor only.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/authentication-policies
NEW QUESTION 7
Which network configuration is required when deploying FortiAuthenticator for portal services?
- A. FortiAuthenticator must have the REST API access enable on port1
- B. One of the DNS servers must be a FortiGuard DNS server
- C. Fortigate must be setup as default gateway for FortiAuthenticator
- D. Policies must have specific ports open between FortiAuthenticator and the authentication clients
Answer: D
Explanation:
When deploying FortiAuthenticator for portal services, such as guest portal, sponsor portal, user portal or FortiToken activation portal, the network configuration must allow specific ports to be open between FortiAuthenticator and the authentication clients. These ports are: TCP 80 for HTTP access
TCP 80 for HTTP access  TCP 443 for HTTPS access
TCP 443 for HTTPS access  TCP 389 for LDAP access
TCP 389 for LDAP access TCP 636 for LDAPS access
TCP 636 for LDAPS access UDP 1812 for RADIUS authentication
UDP 1812 for RADIUS authentication  UDP 1813 for RADIUS accounting
UDP 1813 for RADIUS accounting
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/portal-services#networ
NEW QUESTION 8
Which two statement about the RADIUS service on FortiAuthenticator are true? (Choose two)
- A. Two-factor authentication cannot be enforced when using RADIUS authentication
- B. RADIUS users can migrated to LDAP users
- C. Only local users can be authenticated through RADIUS
- D. FortiAuthenticator answers only to RADIUS client that are registered with FortiAuthenticator
Answer: BD
Explanation:
Two statements about the RADIUS service on FortiAuthenticator are true: RADIUS users can be migrated to LDAP users using the RADIUS learning mode feature. This feature allows FortiAuthenticator to learn user credentials from an existing RADIUS server and store them locally as LDAP users for future authentication requests.
RADIUS users can be migrated to LDAP users using the RADIUS learning mode feature. This feature allows FortiAuthenticator to learn user credentials from an existing RADIUS server and store them locally as LDAP users for future authentication requests. FortiAuthenticator answers only to RADIUS clients that are registered with FortiAuthenticator. A RADIUS client is a device that sends RADIUS authentication or accounting requests to FortiAuthenticator. A RADIUS client must be added and configured on FortiAuthenticator before it can communicate with it.
FortiAuthenticator answers only to RADIUS clients that are registered with FortiAuthenticator. A RADIUS client is a device that sends RADIUS authentication or accounting requests to FortiAuthenticator. A RADIUS client must be added and configured on FortiAuthenticator before it can communicate with it.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/radius-service
NEW QUESTION 9
Which two statements regarding the configuration are true? (Choose two.)
- A. All guest accounts created using the account registration feature will be placed under the Guest_Portal_Users group
- B. All accounts registered through the guest portal must be validated through email
- C. Guest users must fill in all the fields on the registration form
- D. Guest user account will expire after eight hours
Answer: AB
Explanation:
The screenshot shows that the account registration feature is enabled for the guest portal and that the guest group is set to Guest_Portal_Users. This means that all guest accounts created using this feature will be placed under that group1. The screenshot also shows that email validation is enabled for the guest portal and that the email validation link expires after 24 hours. This means that all accounts registered through the guest portal must be validated through email within that time frame1.
References: 1 https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/guest
NEW QUESTION 10
An administrator has an active directory (AD) server integrated with FortiAuthenticator. They want members of only specific AD groups to participate in FSSO with their corporate FortiGate firewalls.
How does the administrator accomplish this goal?
- A. Configure a FortiGate filter on FortiAuthenticatoc
- B. Configure a domain groupings list to identify the desired AD groups.
- C. Configure fine-grained controls on FortiAuthenticator to designate AD groups.
- D. Configure SSO groups and assign them to FortiGate groups.
Answer: D
Explanation:
To allow members of only specific AD groups to participate in FSSO with their corporate FortiGate firewalls, the administrator can configure SSO groups and assign them to FortiGate groups. SSO groups are groups of users or devices that are defined on FortiAuthenticator based on various criteria, such as user group membership, source IP address, MAC address, or device type. FortiGate groups are groups of users or devices that are defined on FortiGate based on various criteria, such as user group membership, firewall policy, or authentication method. By mapping SSO groups to FortiGate groups, the administrator can control which users or devices can access the network resources protected by FortiGate.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/single-sign-on#sso-gro
NEW QUESTION 11
When configuring syslog SSO, which three actions must you take, in addition to enabling the syslog SSO method? (Choose three.)
- A. Enable syslog on the FortiAuthenticator interface.
- B. Define a syslog source.
- C. Select a syslog rule for message parsing.
- D. Set the same password on both the FortiAuthenticator and the syslog server.
- E. Set the syslog UDP port on FortiAuthenticator.
Answer: BCE
Explanation:
To configure syslog SSO, three actions must be taken, in addition to enabling the syslog SSO method: Define a syslog source, which is a device that sends syslog messages to FortiAuthenticator containing user logon or logoff information.
Define a syslog source, which is a device that sends syslog messages to FortiAuthenticator containing user logon or logoff information. Select a syslog rule for message parsing, which is a predefined or custom rule that defines how to extract the user name, IP address, and logon or logoff action from the syslog message.
Select a syslog rule for message parsing, which is a predefined or custom rule that defines how to extract the user name, IP address, and logon or logoff action from the syslog message. Set the syslog UDP port on FortiAuthenticator, which is the port number that FortiAuthenticator listens on for incoming syslog messages.
Set the syslog UDP port on FortiAuthenticator, which is the port number that FortiAuthenticator listens on for incoming syslog messages.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/single-sign-on#syslog-s
NEW QUESTION 12
Which two protocols are the default management access protocols for administrative access for FortiAuthenticator? (Choose two)
- A. Telnet
- B. HTTPS
- C. SSH
- D. SNMP
Answer: BC
Explanation:
HTTPS and SSH are the default management access protocols for administrative access for FortiAuthenticator. HTTPS allows administrators to access the web-based GUI of FortiAuthenticator using a web browser and a secure connection. SSH allows administrators to access the CLI of FortiAuthenticator using an SSH client and an encrypted connection. Both protocols require the administrator to enter a valid username and password to log in.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/system-settings#manag
NEW QUESTION 13
What capability does the inbound proxy setting provide?
- A. It allows FortiAuthenticator to determine the origin source IP address after traffic passes through a proxy for system access,
- B. It allows FortiAuthenticator to act as a proxy for remote authentication servers.
- C. It allows FortiAuthenticator the ability to round robin load balance remote authentication servers.
- D. It allows FortiAuthenticator system access to authenticating users, based on a geo IP address designation.
Answer: A
Explanation:
The inbound proxy setting provides the ability for FortiAuthenticator to determine the origin source IP address after traffic passes through a proxy for system access. The inbound proxy setting allows FortiAuthenticator to use the X-Forwarded-For header in the HTTP request to identify the original client IP address. This can help FortiAuthenticator apply the correct authentication policy or portal policy based on the source IP address.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/system-settings#inboun
NEW QUESTION 14
Which method is the most secure way of delivering FortiToken data once the token has been seeded?
- A. Online activation of the tokens through the FortiGuard network
- B. Shipment of the seed files on a CD using a tamper-evident envelope
- C. Using the in-house token provisioning tool
- D. Automatic token generation using FortiAuthenticator
Answer: A
Explanation:
Online activation of the tokens through the FortiGuard network is the most secure way of delivering FortiToken data once the token has been seeded because it eliminates the risk of seed files being compromised during transit or storage. The other methods involve physical or manual delivery of seed files which can be intercepted, lost, or stolen. References: https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372403/fortitoken
NEW QUESTION 15
......
Recommend!! Get the Full NSE6_FAC-6.4 dumps in VCE and PDF From Certleader, Welcome to Download: https://www.certleader.com/NSE6_FAC-6.4-dumps.html (New 47 Q&As Version)