★ Pass on Your First TRY ★ 100% Money Back Guarantee ★ Realistic Practice Exam Questions
Free Instant Download NEW 2V0-41.23 Exam Dumps (PDF & VCE):
Available on:
https://www.certleader.com/2V0-41.23-dumps.html
Passleader offers free demo for 2V0-41.23 exam. "VMware NSX 4.x Professional", also known as 2V0-41.23 exam, is a VMware Certification. This set of posts, Passing the VMware 2V0-41.23 exam, will help you answer those questions. The 2V0-41.23 Questions & Answers covers all the knowledge points of the real exam. 100% real VMware 2V0-41.23 exams and revised by experts!
Also have 2V0-41.23 free dumps questions for you:
NEW QUESTION 1
What are tour NSX built-in rote-based access control (RBAC) roles? (Choose four.)
- A. Network Admin
- B. Enterprise Admin
- C. Full Access
- D. Read
- E. LB Operator
- F. None
- G. Auditor
Answer: ABEG
Explanation:
https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-26C44DE8-1854-4B06-B6DA-A2FD426
NEW QUESTION 2
Which Is the only supported mode In NSX Global Manager when using Federation?
- A. Controller
- B. Policy
- C. Proxy
- D. Proton
Answer: B
Explanation:
NSX Global Manager is a feature of NSX that allows managing multiple NSX domains across different sites or clouds from a single pane of glass. NSX Global Manager supports Federation, which is a capability that enables synchronizing configuration and policy across multiple NSX domains. Federation has many benefits such as simplifying operations, improving resiliency, and enabling disaster recovery.
The only supported mode in NSX Global Manager when using Federation is Policy mode. Policy mode means that NSX Global Manager acts as a policy manager that defines and distributes global policies to local NSX managers in different domains. Policy mode also allows local NSX managers to have their own local policies that can override or merge with global policies.
NEW QUESTION 3
What are two valid options when configuring the scope of a distributed firewall rule? (Choose two.)
- A. DFW
- B. Tier-1 Gateway
- C. Segment
- D. Segment Port
- E. Group
Answer: CE
Explanation:
* C. Segment. This is correct. A segment is a logical construct that represents a layer 2 broadcast domain and a layer 3 subnet in NSX. A segment can be used to group and connect virtual machines, containers, or bare metal hosts that belong to the same application or service. A segment can also be used as the scope of a distributed firewall rule, which means that the rule will apply to all the traffic that enters or exits the segment12
* E. Group. This is correct. A group is a logical construct that represents a collection of objects in NSX, such as segments, segment ports, virtual machines, IP addresses, MAC addresses, tags, or security policies. A group can be used to define dynamic membership criteria based on various attributes or filters. A group can also be used as the scope of a distributed firewall rule, which means that the rule will apply to all the traffic that matches the group membership criteria32
NEW QUESTION 4
An administrator is configuring service insertion for Network Introspection. Which two places can the Network Introspection be configured? (Choose two.)
- A. Host pNIC
- B. Partner SVM
- C. Tier-0 gateway
- D. Tier-1 gateway
- E. Edge Node
Answer: AB
Explanation:
Network Introspection is a service insertion feature that allows third-party network security services to
monitor and analyze the traffic between virtual machines. Network Introspection can be configured on the host pNIC or on the partner SVM, depending on the type of service and the deployment model. The host pNIC configuration is used for services that require traffic redirection from the physical network to the service virtual machine. The partner SVM configuration is used for services that require traffic redirection from the virtual network to the service virtual machine. Network Introspection cannot be configured on the Tier-0 or Tier-1 gateways, as they are not part of the data plane where the service insertion occurs. Network Introspection also cannot be configured on the edge node, as it is a logical construct that hosts the Tier-0 and Tier-1 gateways. References: Distributed Service Insertion, NSX Securing “Anywhere” Part IV
NEW QUESTION 5
Which statement is true about an alarm in a Suppressed state?
- A. An alarm can be suppressed for a specific duration in seconds.
- B. An alarm can be suppressed for a specific duration in days.
- C. An alarm can be suppressed for a specific duration in minutes.
- D. An alarm can be suppressed for a specific duration in hours.
Answer: D
Explanation:
The answer is D. An alarm can be suppressed for a specific duration in hours.
According to the VMware NSX documentation, an alarm can be in one of the following states: Open, Acknowledged, Suppressed, or Resolved12
An alarm in a Suppressed state means that the status reporting for this alarm has been disabled by the user for a user-specified duration12
When a user moves an alarm into a Suppressed state, they are prompted to specify the duration in hours. After the specified duration passes, the alarm state reverts to Open. However, if the system determines the condition has been corrected, the alarm state changes to Resolved13
To learn more about how to manage alarm states in NSX, you can refer to the following resources:  VMware NSX Documentation: Managing Alarm States 1
VMware NSX Documentation: Managing Alarm States 1 VMware NSX Documentation: View Alarm Information 2
VMware NSX Documentation: View Alarm Information 2 VMware NSX Intelligence Documentation: Manage NSX Intelligence Alarm States 3 https://docs.vmware.com/en/VMware-NSX-Intelligence/1.2/user-guide/GUID-EBD3C5A8-F9AB-4A22-BA40-
VMware NSX Intelligence Documentation: Manage NSX Intelligence Alarm States 3 https://docs.vmware.com/en/VMware-NSX-Intelligence/1.2/user-guide/GUID-EBD3C5A8-F9AB-4A22-BA40-
NEW QUESTION 6
When collecting support bundles through NSX Manager, which files should be excluded for potentially containing sensitive information?
- A. Controller Files
- B. Management Files
- C. Core Files
- D. Audit Files
Answer: C
Explanation:
According to the VMware NSX Documentation1, core files and audit logs can contain sensitive information and should be excluded from the support bundle unless requested by VMware technical support. Controller files and management files are not mentioned as containing sensitive information.
NEW QUESTION 7
Which two choices are use cases for Distributed Intrusion Detection? (Choose two.)
- A. Use agentless antivirus with Guest Introspection.
- B. Quarantine workloads based on vulnerabilities.
- C. Identify risk and reputation of accessed websites.
- D. Gain Insight about micro-segmentation traffic flows.
- E. Identify security vulnerabilities in the workloads.
Answer: BE
Explanation:
According to the VMware NSX Documentation, these are two of the use cases for Distributed Intrusion Detection, which is a feature of NSX Network Detection and Response: Quarantine workloads based on vulnerabilities: You can use Distributed Intrusion Detection to detect vulnerabilities in your workloads and apply quarantine actions to isolate them from the network until they are remediated.
Quarantine workloads based on vulnerabilities: You can use Distributed Intrusion Detection to detect vulnerabilities in your workloads and apply quarantine actions to isolate them from the network until they are remediated. Identify security vulnerabilities in the workloads: You can use Distributed Intrusion Detection to scan your workloads for known vulnerabilities and generate reports that show the severity, impact, and remediation steps for each vulnerability.
Identify security vulnerabilities in the workloads: You can use Distributed Intrusion Detection to scan your workloads for known vulnerabilities and generate reports that show the severity, impact, and remediation steps for each vulnerability.
NEW QUESTION 8
Which NSX CLI command is used to change the authentication policy for local users?
- A. Set cli-timeout
- B. Get auth-policy minimum-password-length
- C. Set hardening- policy
- D. Set auth-policy
Answer: D
Explanation:
According to the VMware NSX Documentation4, the set auth-policy command is used to change the authentication policy settings for local users, such as password length, lockout period, and maximum authentication failures. The other commands are either used to view the authentication policy settings (B), change the CLI session timeout (A), or change the hardening policy settings ©.
NEW QUESTION 9
Which two of the following features are supported for the Standard NSX Application Platform Deployment? (Choose two.)
- A. NSX Intrusion Detection and Prevention
- B. NSX Intelligence
- C. NSX Network Detection and Response
- D. NSX Malware Prevention Metrics
- E. NSX Intrinsic Security
Answer: CD
Explanation:
The NSX Application Platform Deployment features are divided into three form factors: Evaluation, Standard, and Advanced. Each form factor determines which NSX features can be activated or installed on the platform1. The Evaluation form factor supports only NSX Intelligence, which provides network visibility and analytics for NSX-T environments2. The Standard form factor supports both NSX Intelligence and NSX Network Detection and Response, which provides network threat detection and response capabilities for
NSX-T environments3. The Advanced form factor supports all four features: NSX Intelligence, NSX Network Detection and Response, NSX Malware Prevention, and NSX Metrics1.
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/nsx-application-platform/GUID-85CD2728-8081
NEW QUESTION 10
What is the VMware recommended way to deploy a virtual NSX Edge Node?
- A. Through the OVF command line tool
- B. Through the vSphere Web Client
- C. Through automated or Interactive mode using an ISO
- D. Through the NSXUI
Answer: D
Explanation:
Through the NSX UI. According to the VMware NSX Documentation2, you can deploy NSX Edge nodes as virtual appliances through the NSX UI by clicking Add Edge Node and providing the required information. The other options are either outdated or not applicable for virtual NSX Edge nodes.
https://docs.vmware.com/en/VMware-NSX/4.1/installation/GUID-E9A01C68-93E7-4140-B306-19CD6806199
NEW QUESTION 11
Which two commands does an NSX administrator use to check the IP address of the VMkernel port for the Geneve protocol on the ESXi transport node? (Choose two.)
- A. esxcfg-nics -1l
- B. esxcli network ip interface ipv4 get
- C. esxcli network nic list
- D. esxcfg-vmknic -1l
- E. net-dvs
Answer: BD
Explanation:
To check the IP address of the VMkernel port for the Geneve protocol on the ESXi transport node, an NSX administrator can use the following commands: esxcli network ip interface ipv4 get: This command displays the IPv4 configuration of all VMkernel interfaces on the host, including their IP addresses, netmasks, and gateways. The Geneve protocol uses a VMkernel interface named geneve0 by default1
esxcli network ip interface ipv4 get: This command displays the IPv4 configuration of all VMkernel interfaces on the host, including their IP addresses, netmasks, and gateways. The Geneve protocol uses a VMkernel interface named geneve0 by default1 esxcfg-vmknic -l: This command lists all VMkernel interfaces on the host, along with their MAC addresses, MTU, and netstack. The Geneve protocol uses a netstack named nsx-overlay by default
esxcfg-vmknic -l: This command lists all VMkernel interfaces on the host, along with their MAC addresses, MTU, and netstack. The Geneve protocol uses a netstack named nsx-overlay by default
NEW QUESTION 12
Which two choices are solutions offered by the VMware NSX portfolio? (Choose two.)
- A. VMware Tanzu Kubernetes Grid
- B. VMware Tanzu Kubernetes Cluster
- C. VMware NSX Advanced Load Balancer
- D. VMware NSX Distributed IDS/IPS
- E. VMware Aria Automation
Answer: CD
Explanation:
VMware NSX is a portfolio of networking and security solutions that enables consistent policy, operations, and automation across multiple cloud environments1
The VMware NSX portfolio includes the following solutions: VMware NSX Data Center: A platform for data center network virtualization and security that delivers a complete L2-L7 networking stack and overlay services for any workload1
VMware NSX Data Center: A platform for data center network virtualization and security that delivers a complete L2-L7 networking stack and overlay services for any workload1 VMware NSX Cloud: A service that extends consistent networking and security to public clouds such as AWS and Azure1
VMware NSX Cloud: A service that extends consistent networking and security to public clouds such as AWS and Azure1 VMware NSX Advanced Load Balancer: A solution that provides load balancing, web application
VMware NSX Advanced Load Balancer: A solution that provides load balancing, web application
firewall, analytics, and monitoring for applications across any cloud12 VMware NSX Distributed IDS/IPS: A feature that provides distributed intrusion detection and prevention for workloads across any cloud12
VMware NSX Distributed IDS/IPS: A feature that provides distributed intrusion detection and prevention for workloads across any cloud12 VMware NSX Intelligence: A service that provides planning, observability, and intelligence for network and micro-segmentation1
VMware NSX Intelligence: A service that provides planning, observability, and intelligence for network and micro-segmentation1 VMware NSX Federation: A capability that enables multi-site networking and security management with consistent policy and operational state synchronization1
VMware NSX Federation: A capability that enables multi-site networking and security management with consistent policy and operational state synchronization1 VMware NSX Service Mesh: A service that connects, secures, and monitors microservices across multiple clusters and clouds1
VMware NSX Service Mesh: A service that connects, secures, and monitors microservices across multiple clusters and clouds1 VMware NSX for Horizon: A solution that delivers secure desktops and applications across any device, location, or network1
VMware NSX for Horizon: A solution that delivers secure desktops and applications across any device, location, or network1 VMware NSX for vSphere: A solution that provides network agility and security for vSphere environments with a built-in console in vCenter1
VMware NSX for vSphere: A solution that provides network agility and security for vSphere environments with a built-in console in vCenter1 VMware NSX-T Data Center: A platform for cloud-native applications that supports containers, Kubernetes, bare metal hosts, and multi-hypervisor environments1
VMware NSX-T Data Center: A platform for cloud-native applications that supports containers, Kubernetes, bare metal hosts, and multi-hypervisor environments1
VMware Tanzu Kubernetes Grid and VMware Tanzu Kubernetes Cluster are not part of the VMware NSX portfolio. They are solutions for running Kubernetes clusters on any cloud3
VMware Aria Automation is not a real product name. It is a fictional name that does not exist in the VMware portfolio.
https://blogs.vmware.com/networkvirtualization/2020/01/nsx-hero.html/
NEW QUESTION 13
Which two CLI commands could be used to see if vmnic link status is down? (Choose two.)
- A. esxcfg-nics -1
- B. excli network nic list
- C. esxcli network vswitch dvs wmare list
- D. esxcfg-vmknic -1
- E. esxcfg-vmsvc/get.network
Answer: AB
Explanation:
esxcfg-nics -l and esxcli network nic list are two CLI commands that can be used to see the vmnic link status on an ESXi host. Both commands display information such as the vmnic name, driver, link state, speed, and duplex mode. The link state can be either Up or Down, indicating whether the vmnic is connected or not. For example, the output of esxcfg-nics -l can look like this:
Name PCI Driver Link Speed Duplex MAC Address MTU Description
vmnic0 0000:02:00.0 igbn Up 1000Mbps Full 00:50:56:01:2a:3b 1500 Intel Corporation I350 Gigabit Network Connection vmnic1 0000:02:00.1 igbn Down 0Mbps Half 00:50:56:01:2a:3c 1500 Intel Corporation I350 Gigabit Network Connection
NEW QUESTION 14
The security administrator turns on logging for a firewall rule. Where is the log stored on an ESXi transport node?
- A. /var/log/vmware/nsx/firewall.log
- B. /var/log/messages.log
- C. /var/log/dfwpktlogs.log
- D. /var/log/fw.log
Answer: C
Explanation:
The log for a firewall rule on an ESXi transport node is stored in the /var/log/dfwpktlogs.log file. This file contains information about the packets that match or do not match the firewall rules, such as the source and destination IP addresses, ports, protocols, actions, and rule IDs. The log file can be viewed using the esxcli network firewall get command or the vSphere Client.
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/administration/GUID-D57429A1-A0A9-42BE-A
NEW QUESTION 15
Refer to the exhibit.
An administrator configured NSX Advanced Load Balancer to load balance the production web server traffic, but the end users are unable to access the production website by using the VIP address.
Which of the following Tier-1 gateway route advertisement settings needs to be enabled to resolve the problem? Mark the correct answer by clicking on the image.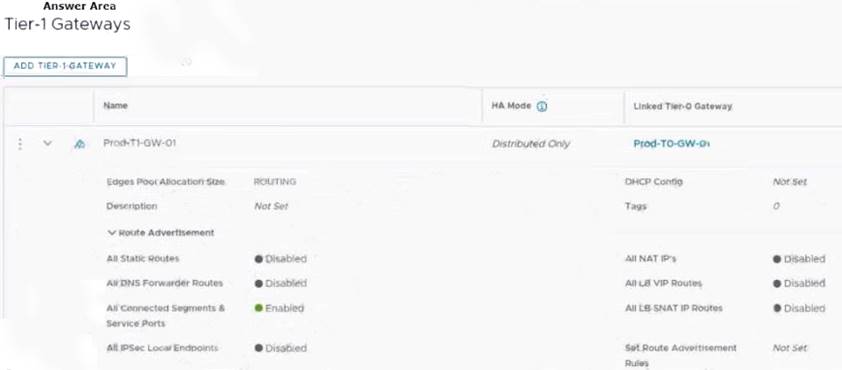
Solution:
The correct answer is to enable the option All LB VIP Routes on the Tier-1 gateway route advertisement settings. This option allows the Tier-1 gateway to advertise the NSX Advanced Load Balancer LB VIP routes to the Tier-0 gateway and other peer routers, so that the end users can reach the production website by using the VIP address1. The other options are not relevant for this scenario.
To mark the correct answer by clicking on the image, you can click on the toggle switch next to All LB VIP Routes to turn it on. The switch should change from gray to blue, indicating that the option is enabled. See the image below for reference:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
Which three protocols could an NSX administrator use to transfer log messages to a remote log server? (Choose three.)
- A. HTTPS
- B. TCP
- C. SSH
- D. UDP
- E. TLS
- F. SSL
Answer: BDE
Explanation:
An NSX administrator can use TCP, UDP, or TLS protocols to transfer log messages to a remote log server. These protocols are supported by NSX Manager, NSX Edge, and hypervisors for remote logging. A Log Insight log server supports all these protocols, as well as LI and LI-TLS, which are specific to Log Insight and optimize network usage. HTTPS, SSH, and SSL are not valid protocols for remote logging in NSX-T Data Center. References: : VMware NSX-T Data Center Administration Guide, page 102. : VMware Docs: Configure Remote Logging
NEW QUESTION 17
An NSX administrator is creating a Tier-1 Gateway configured In Active-Standby High Availability Mode. In the event of node failure, the failover policy should not allow the original tailed node to become the Active node upon recovery.
Which failover policy meets this requirement?
- A. Non-Preemptive
- B. Preemptive
- C. Enable Preemptive
- D. Disable Preemptive
Answer: A
Explanation:
According to the VMware NSX Documentation, a non-preemptive failover policy means that the original failed node will not become the active node upon recovery, unless the current active node fails again. This policy can help avoid unnecessary failovers and ensure stability.
The other options are either incorrect or not available for this configuration. Preemptive is the opposite of non-preemptive, meaning that the original failed node will become the active node upon recovery, if it has a higher priority than the current active node. Enable Preemptive and Disable Preemptive are not valid options for the failover policy, as the failover policy is a drop-down menu that only has two choices: Preemptive and Non-Preemptive.
NEW QUESTION 18
......
P.S. Easily pass 2V0-41.23 Exam with 106 Q&As Downloadfreepdf.net Dumps & pdf Version, Welcome to Download the Newest Downloadfreepdf.net 2V0-41.23 Dumps: https://www.downloadfreepdf.net/2V0-41.23-pdf-download.html (106 New Questions)